Authentication
Dubbo provides comprehensive mechanisms to build a secure microservices communication system, also known as a Zero Trust system. This includes:
- Preventing man-in-the-middle attacks by offering identity authentication (Authentication) and TLS-based encrypted communication.
- Controlling inter-service access authorization (Authorization) with mechanisms like mTLS and permission checks.
This document will guide you through leveraging Dubbo’s security features to build a Zero Trust system for your microservices, focusing on authentication, transparent encryption, authorization, and auditing. Since Zero Trust is a comprehensive approach, you may need another infrastructure, such as certificate management and security policy control.
Note: The scope of this document does not include certificate generation and distribution. We assume you already have an infrastructure in place for certificate management. Hence, we will focus on Dubbo’s authentication and authorization mechanisms and processes. If you lack such infrastructure, we recommend using a service mesh architecture like Istio for certificate management and security policies.
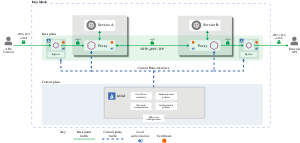
Architecture
A complete Zero Trust system comprises multiple components:
- A Root Certificate Authority (CA) to manage keys and certificates.
- A security policy management and distribution center to send real-time policies to data plane components:
- Authentication policies
- Authorization policies
- Secure Naming Information
- Data plane components (Dubbo) responsible for identification, encryption, and policy enforcement.
- A suite of tools and ecosystems to complete security audits and data link monitoring.
In a service mesh deployment like Istio, the control plane typically handles security policies and certificates, interacting with infrastructure like the Kubernetes API Server to distribute configuration data to Dubbo or other data plane components.
Here is a comprehensive architecture diagram for Dubbo Zero Trust:
Authentication
Dubbo provides two modes of authentication:
- Channel Authentication: Dubbo supports TLS-based HTTP/2 and TCP communication. You can enable TLS through Channel Authentication API or control plane policies for server identity authentication and data link encryption. Additionally, you can enable mTLS for client-server mutual authentication. This is a service-to-service mode of authentication.
- Request Authentication: Dubbo offers APIs to attach user identity credentials (like JWT tokens) in the request context. Dubbo automatically recognizes these identity tokens for permission checks. You can also customize these tokens, like OAuth2 access tokens. This is an end-user mode of authentication, representing the identity of the user logged into the system.
Architecture
In Istio mode, Dubbo’s authentication mechanism automatically interfaces with the Istio control plane through xDS. Certificates and authentication policies generated by the Istio control plane are automatically sent to the Dubbo data plane, which applies them to all subsequent data communications.
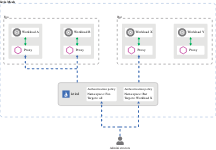
Dubbo mTLS Flow
In Istio deployments, you can enable or disable Channel Authentication’s mutual authentication through control plane policies. The workflow for mutual authentication is as follows:
- Istio sends authentication policies to enable mutual authentication.
- The Dubbo client initiates a mutual TLS handshake with the server, performing a secure naming check to validate the server’s identity.
- A mutual mTLS link is established between the client and server for encrypted communication.
- The Dubbo server recognizes the client’s identity and checks whether it has the permission to access the corresponding resource.
Authentication Policies
For specific rules supported by Istio, Dubbo fully supports Istio-defined authentication policies.
Authorization
Dubbo has abstracted an authorization extension mechanism but currently only supports the Istio system. Thus, its authorization capabilities are equivalent to those described in the official Istio documentation.
Architecture
Dubbo receives user-configured authorization policies from the Istio control plane through xDS. When a request reaches a Dubbo instance, the built-in authorization engine matches the request parameters and user identity against the policy. If the match is successful, access is granted; otherwise, it’s denied.
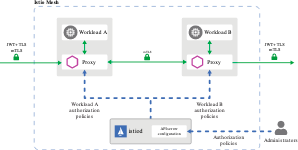
Authorization Policies
For specific rules supported by Istio, Dubbo fully supports Istio-defined authorization policies.
Dubbo Authentication API
Dubbo defines an authentication API. For general use cases, developers can enable TLS/mTLS through this API. However, in an Istio control plane deployment, Dubbo automatically recognizes the certificates and authentication policies sent by Istio, so no special configuration is needed on the Dubbo side.
Whether or not you use the Istio control plane, JWT tokens for Request Authentication still need to be specified programmatically in Dubbo.
For language-specific API definitions, please refer to the respective SDK documentation:
Sample Tasks
Please visit the following Dubbo Task Examples for hands-on practice with security policies.
